Production
Hacking Exposed & Spin-Offs
You needn't have been a tech visionary to profit off the explosion of desktop computing in the late 90s and the ensuing dot-com bubble. You just needed to publish How-To computer books. No one was better equipped to fill this role than publishing behemoth McGraw-Hill. I was part of a production team at its Osborne technology division in Berkeley and Emeryville that generated 175+ titles in a single year (2003). The computer book boom was a license to print money.
As Associate Production Architect, I had a key role in crafting several book series, including Hacking Exposed. The initial run sold out in its first month—and close to 600,000 copies (translated in 30 languages) have been sold over the course of seven editions. The original title spawned several spin-offs—Hacker’s Challenge, Incident Response, Anti-Hacker Took Kit, and Hack Notes.
The following is a peek inside the design and production mind-set.
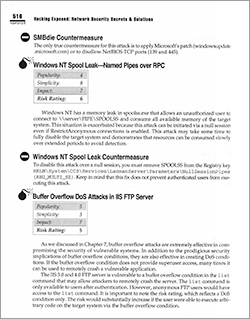
PRINCIPAL TITLE
Hacking Exposed
The book jackets are eye-catching, but it's what is inside that counts. We hit pay dirt with a formula that intersperses Attacks (designated by bomb icons and Risk Rating tables) with Countermeasures (Do-Not-Enter symbols).
On the technical end: The icons were rendered into fonts that flow with the text. The authors wrote to a template. Word styles were converted into layout-friendly mark-up code. Scripts automatically positioned illustrations and formatted tables. The composition team applied the finishing touches.
The net result: a highly-automated production process. Another net result: $7 million in revenues through four editions for the flagship title.
SPIN-OFF
Incident Response
After the digital marauders have struck, where do you look and what do you do? Incident Response is about forensics: how to gather and preserve the evidence. It presents case studies and “eye-witness” accounts...and tells how to respond to and prevent computer crime.
The design is aswarm with special elements: What Can Happen (using a badge icon), Where to Look for Evidence (fingerprint image), Law Enforcement Tip (footprint), Crime Scene (“Crime Scene Do-Not-Cross” tape), and Eye Witness Report (eyeball). Special character tags and negative kerning were used so superscripted footnote numbers would not disturb the monospacing of computer code.

SPIN-OFF
Anti-Hacker Toolkit
Other security books talk the talk, Anti-Hacker Toolkit delivers the tools to combat hackers. Not for the meek, it is definitely for the geek—with command-line programs like John the Ripper, Snort, Cryptcat, and Back Orifice (many on a bonus CD, others downloadable). Authors Jones, Johnson and Shema are to computer security what Bob Vila is to home improvement. A spin-off, Anti-Spam Tool Kit, focuses on tools to combat unwanted e-mail.
The book’s interior is crafted to mirror the cover’s industrial look—from Machine font to 3-D icons. But the real feat was assembling a bonus CD with 30 anti-hacking tools—with PC, Mac and Unix utilities all on the same disc—and links to another 70 programs on the Web.

SPIN-OFF
Hacker's Challenge
Like the cover image portrays, Hacker’s Challenge presents real-life hacking accounts that had security experts fit to be tied. Readers are challenged to figure out what the Black Hats were doing, and to match wits with the defenders. Web defacements, DNS tunneling, packet sniffing—it’s mystery reading for the digital age.
The book’s format juxtaposes 20 hacking Challenges in Part I with 20 Solutions in Part II. Hacking scenarios are chronologically reenacted, with dates and times marked off in LCD lettering.
Wide margins encouraged readers to jot notes.
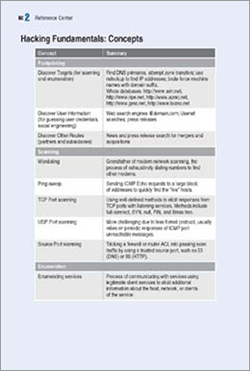
SPIN-OFF
Hack Notes
Most computer books could double as boat anchors. Not Hack Notes—slim 6"x9" reference guides designed to be toted around by IT pros. The books cut to the chase with tables, screenshots, and other handy data to foil and fix security breaches on various platforms.
The challenge: squeezing the maximum amount of content into the smallest of space (a 6"x9" trim size).
To the rescue: tables. These reference books are jam-packed with tabular information, including special Reference Center inserts. The design uses diagonal watermarks across page tops and bottoms, striping to add readability to tables, and a variety of special elements: Hot tips (log/fire icon), Knowledge to Remember (information symbol), Hack (sword icon), and Defense (shield). En garde!